IoT Vulnerability Assessment
Secure Your IoT Ecosystem
Revolutionizing Efficiency and Convenience, While Navigating Cyber Vulnerabilities
In our evolving digital landscape, the rise of embedded devices and smart technologies is revolutionizing the way we interact with the world. With applications ranging from industrial automation to smart home technologies, these devices are redefining efficiency and convenience in unprecedented ways. However, with the surge in advanced, connected tech, one major challenge emerges – their vulnerability to cyber-attacks.
The Hidden Risks of Embedded Devices
Our world is teeming with a vast array of embedded devices, and while they bring immense benefits, their compact size and limited capabilities often make them a lucrative target for cybercriminals. Further exacerbating the issue is the limited feasibility of continually updating and automating security measures for these devices, as is standard for traditional IT systems. As a result, the onus of identifying and addressing these vulnerabilities becomes crucial.
The Domino Effect in Smart Device Security
Additionally, many smart devices are constructed without intrinsic security measures, amplifying their susceptibility to cyber threats. In an interconnected IoT ecosystem, a single compromised device can endanger the entire network. Understanding your network’s exposure and mapping out the potential attack surface becomes a non-negotiable priority.
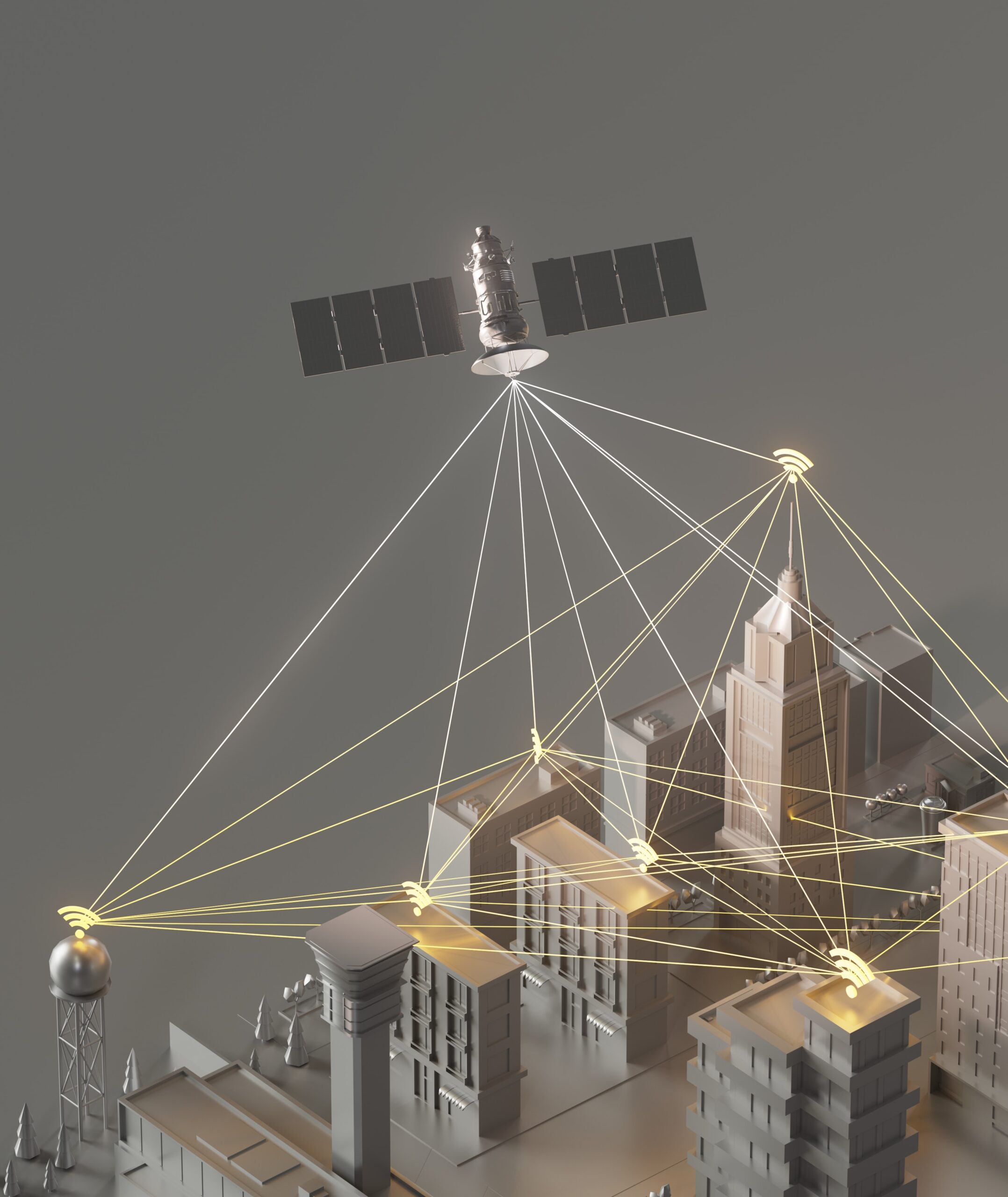

Proactively Combating IoT Vulnerabilities Head-On
We’re here to safeguard your IoT ecosystem. As part of our comprehensive IoT Vulnerability Assessment services, we deliver exhaustive security testing for all your devices. Backed by a team of professional security experts adept at employing cutting-edge techniques and tools, we meticulously identify and mitigate potential vulnerabilities and risk points. We are committed to offering the most optimal and practical solutions, empowering you to enjoy peace of mind, knowing that your IoT devices are shielded against potential security threats.
Whether you’re an IoT device manufacturer, a homeowner with a suite of intelligent tech, or a business leveraging IoT/IIoT, our team of IoT security experts is at your service. We provide top-tier vulnerability assessment services designed to keep you perpetually shielded from threats.
Are you ready to fortify your IoT devices? Don’t wait for a cyber-attack to catch you off guard. Get in touch with us today to explore our IoT security solutions, and let us help you keep your world connected, intelligent, and above all, secure.

Our Comprehensive Approach to IoT Vulnerability Assessment
In the current digital age, maintaining the security of your IoT devices is crucial. Our IoT Security Assessment services thoroughly examine examination your IoT devices, fortifying them against potential cyber threats. We are committed to detecting and mitigating the vulnerabilities that could leave your devices at risk. A few of the examined components in a comprehensive test will include the following:
Cloud Components Assessment
Cloud components play a pivotal role in IoT security. We delve into the intricacies of your embeeded device backend cloud infrastructure and communications channels to identify potential security gaps for a safer, more secure ecosystem.
Web Applications Evaluation
Web applications running on embeeded devices are often prime targets for cyber threats. Our experts will meticulously examine your device to detect any potential vulnerabilities, such as cross-site scripting or SQL injections. We effectively unravel these issues, enhancing your web applications’ overall security and resilience.
Mobile Application Review
If your IoT devices operate using a mobile application, ensuring its securely functioning is essential. We perform an exhaustive security assessment of your mobile apps, highlighting vulnerabilities such as insecure data storage, permission overreach, code vulnerabilities and more
Embedded Firmware Security Assessment
The state of your IoT devices’ embedded firmware is critical to its security. We thoroughly examine the firmware to check for both known and unknown security vulnerabilities. Our assessment process provides insights into the firmware’s current state and host components and delivers comprehensive recommendations and risk mitigations for relevant findings
